The dark web is a part of the internet not indexed by standard search engines like Google or Bing. Unlike the visible, "surface web," the dark web operates through overlay networks—most notably, Tor (The Onion Router)—that keep users anonymous.
To access the dark web, users must install a specialized browser that supports these protocols, such as the Tor Browser or use special operating systems and networks.
In this guide, we’ll explore The Dark Web's Structure, History, Benefits & Risks, and How to Stay Safe if you choose to visit.
"The dark web is not inherently evil. Like any tool, it depends on the hands that wield it." - John McAfee*, Computer Programmer and Cybersecurity Pioneer
*Yes, McAfee was a little nutty, but it’s still a good quote.
Your Ultimate Dark Web Guide
Dark Web Structure
As mentioned above, the dark web isn't accessible through standard search engines and requires special software to use and navigate.
And while it indeed houses illegal activities, it’s also a place of privacy and free expression: journalists use it to exchange sensitive information, citizens use it to circumvent intense levels of censorship, and activists, whistle blowers and many others use it in order to obtain the highest levels of anonymity possible.
Who Created the Dark Web?
Initial work on the dark web began in 2000 by University of Edinburgh student Ian Clarke, who created the "Distributed Decentralised Information Storage and Retrieval System."
Clarke aimed to build a method to anonymously communicate and share files online. This project, known as Freenet, was the groundwork for the Tor Project, which started in 2002 and launched the Tor Browser in 2008.
With the creation of Tor, users could now browse the internet completely anonymously and explore sites deemed part of the "dark web."
Tor (The Onion Router) enabled anonymous communication by routing traffic through multiple volunteer-operated servers. Initially developed by the U.S. Naval Research Laboratory in the mid-1990s and later managed by the non-profit Tor Project, Tor's primary purpose was to protect online privacy and enable secure communication for intelligence purposes.
Evolution of the Dark Web
Over the years, the dark web grew in popularity. While initially a government project, it became a tool for journalists, activists, and, unfortunately, criminals. The accessibility of Tor has helped it evolve into a multifaceted ecosystem with both positive and negative uses.
However, while Tor is the most well known tool for the public to access the dark web, it was not the first. And there are now other networks and tools that provide access to the dark web, such as I2P, ZeroNet and Lokinet.
Is it Illegal to Access the Dark Web?
Accessing the dark web itself isn’t illegal in most countries. However, certain activities, like purchasing illegal items or engaging in prohibited activities, are punishable by law.
Surface Web vs. Deep Web vs. Dark Web
Before we go any further, let’s make sure we are all clear on the key terms to describe the various parts of the internet:

Surface Web
The surface web is the portion of the internet we interact with daily, accessible via search engines and composed of publicly indexed sites. This is the internet you probably know and love (and hate). Unfortunately, the surface web is full of trackers, ads and other junk that you would probably rather avoid.
Deep Web
The deep web encompasses unindexed content, including databases, academic journals, subscription services, and password-protected sites like banking portals. The deep web is not inherently sinister; it simply includes all content that isn’t open to the public. It’s accessible with your regular browser as long as you have access.
Dark Web
The dark web is a smaller segment of the deep web and requires specialized software for access. Unlike the deep web, it places a high emphasis on user anonymity and often hosts sensitive or illicit content.
How Does the Dark Web Work?
The dark web uses specialized technology designed to anonymize users. The Tor network, for example, uses multiple layers of encryption (hence the term "onion routing") to hide the origin and destination of data. This means data bounces through a series of volunteer-run nodes around the world, making it almost impossible to track.
Major organizations, including intelligence agencies, use Tor to safeguard sensitive communications. For example, the CIA operates a .onion site on the dark web to facilitate secure communication channels for whistleblowers and informants worldwide.
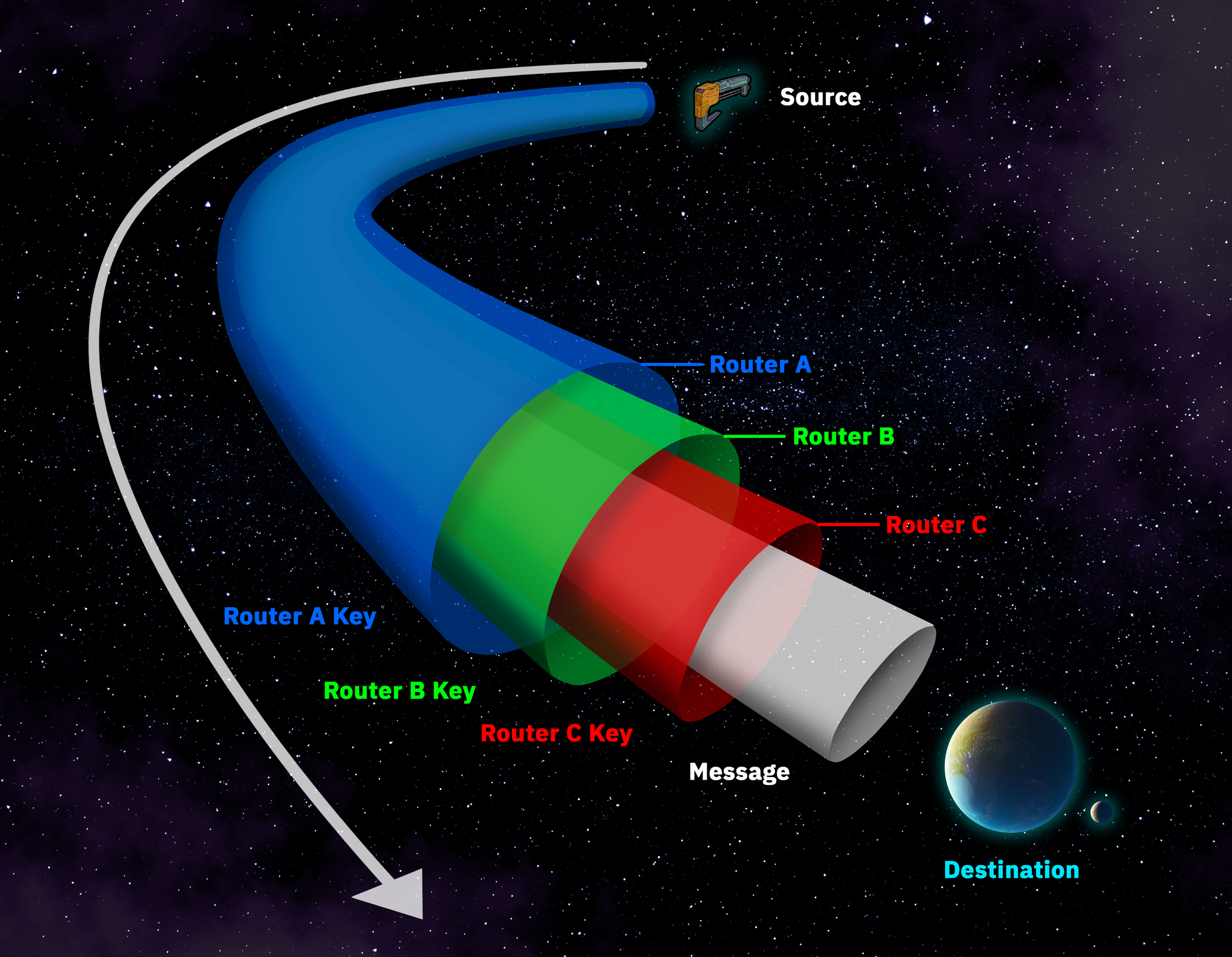
Onion routing enables users to access .onion sites on the dark web, where each "layer" of encryption is decrypted only by specific nodes on the route, hiding the sender and receiver.
Imagine sending a letter through a chain of post offices, each one placing it in a new envelope with a different address, until it reaches its final destination. Each layer in onion routing works like these envelopes, ensuring that only the final recipient knows where the letter originated.
This structure ensures anonymity but also attracts individuals looking to evade traditional tracking, monitoring and censorship.
How to Access the Dark Web: Other Types of Tools and Encryption
Remember, though Tor is the most well-known, there are other common ways to access the dark web:
- I2P (Invisible Internet Project): A separate network focusing on secure peer-to-peer connections and privacy. Used mainly for hosting hidden services. This method uses end-to-end encryption between peers with multiple layers, similar to Tor. I2P employs ElGamal/AES encryption for secure tunnel building, which maintains anonymity by routing data through layered, bidirectional tunnels.
- Freenet: A decentralized, censorship-resistant platform that requires specific software to access. It’s often used for anonymous file sharing and forums. Freenet implements public-key encryption using AES and SHA1/SHA256 to secure data sharing. Nodes communicate in an encrypted, decentralized network, with files stored in encrypted fragments across multiple nodes to ensure security and data integrity.
- Tails OS: An operating system specifically built for anonymity; routes all internet traffic through Tor and doesn’t leave traces on the device. Tails also uses LUKS (Linux Unified Key Setup) encryption for persistent storage to protect any saved data.
Each method comes with varying levels of privacy, security, and ease of use.
What Can You Find on the Dark Web?
The dark web, just like the surface web, hosts a mix of content. While there are illegal goods and services, from contraband and hacked data to banned media and political documents, you’ll also find non-criminal forums, news sites, research databases, and marketplaces dedicated to privacy-focused tools. It also serves a very important role for those in need of life-critical privacy.
Anonymity-Driven Services
Platforms such as whistleblower sites, political discussion forums, and alternative media outlets make the dark web a haven for those seeking to avoid censorship. Journalists, activists, and individuals in repressive regimes use it to share information without fear of surveillance or reprisal. Without the dark web, many of these folks would not have the ability to share and access critical information.
Think of dark web forums as exclusive clubs where only those with the right credentials (like specific browser configurations) can gain entry. This exclusivity emphasizes the level of privacy, and sometimes secrecy, that users seek.
What is the Dark Web Used For? The Good and Bad Sides of the Dark Web Examined
The Dark Web may have a bit of a seedy reputation, but let's take a closer look at the good and the bad sides, shall we?
“Privacy is a feature of freedom, and anonymity is a feature of privacy. So, the dark web is one of those things that has both upsides and downsides for privacy." - Garry Kasparov, Former World Chess Champion and Cybersecurity Advocate
The Good Sides of The Dark Web:
There are many legitimate reasons to access the dark web:
- Privacy Protection: Some users are drawn to the dark web because it shields their digital footprint, offering a refuge from the extensive data tracking found on the surface web.
- Whistleblowing: It serves as an open environment for those censored elsewhere. Organizations like Privacy International and the Electronic Frontier Foundation (EFF) champion the dark web's potential for privacy and free expression, especially for activists, whistle blowers and journalists. Platforms like SecureDrop allow individuals to submit documents anonymously to news organizations.
- Free Speech: In regions where internet censorship is enforced, the dark web provides a space for free expression without governmental oversight.
“Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say.” - Edward Snowden, Whistleblower and Privacy Advocate
Some significant examples of the use of the dark web as a vital lifeline for free expression, journalism, and activism include:
- Edward Snowden (2013) – Snowden, a former NSA contractor, used encrypted dark web channels and platforms like Tor to communicate with journalists and leak classified information about government surveillance. Snowden’s disclosures led to global discussions on privacy and government overreach.
- WikiLeaks (2006) – Founded by Julian Assange, WikiLeaks often uses Tor and other dark web tools to maintain anonymity and avoid censorship. The platform has published confidential government documents and exposed corporate misconduct, using the dark web as a means to enable secure whistleblowing.
- Chinese Activists and Journalists – In countries with strict censorship, such as China, journalists and activists turn to the dark web to evade government surveillance. The dark web provides a way for individuals to share information, communicate, and organize protests without risking exposure on regular internet platforms monitored by the state.
- Mexican Journalists Covering Cartels – In Mexico, where violence against journalists is high, reporters covering drug cartels and government corruption sometimes use dark web platforms to protect their sources and communicate anonymously. This is especially important for journalists working in regions where revealing sensitive information can have severe consequences.
- Middle Eastern and North African Activists – During the Arab Spring, many activists in countries like Tunisia and Egypt relied on dark web tools to communicate outside of government scrutiny. The Tor network and similar tools helped protect their identities and enabled them to mobilize support.
- Citizen Journalists in Iran – In Iran, where free press is restricted, citizen journalists use dark web forums to share footage and reports that reveal what is happening on the ground. The dark web provides them with an outlet for information that would otherwise be suppressed.
The Bad Sides of The Dark Web:
While the dark web has its benefits, it also hosts illegal activities:
- Black Markets: Some dark web marketplaces sell contraband items, ranging from drugs to weapons.
- Data Leaks: Hackers often sell stolen information, like credit card details or login credentials, on the dark web.
- Malicious Software: Malware, ransomware, and other harmful software are available for sale, posing a threat to cybersecurity.
Here are a few examples of some of the nefarious activities you may have heard of happening on the dark web:
- Silk Road: Silk Road was the first major black market on the dark web, launched in 2011 by Ross Ulbricht. It enabled the anonymous sale of illegal drugs, weapons, and other illicit goods using Bitcoin and Tor, becoming infamous before its shutdown by the FBI in 2013.
- Ashley Madison Data Leak: In 2015, hackers exposed millions of records from Ashley Madison, a dating platform for extramarital affairs. The leak included users' personal information and payment details, sparking privacy concerns and personal fallout for those affected. The stolen data was distributed and shared on the dark web.
- Wannacry Ransomware: Wannacry ransomware, originating on the dark web, encrypted files across infected computers and demanded Bitcoin payments for decryption. This ransomware attack in 2017 affected organizations globally, including hospitals and government systems.
Risks of Using the Dark Web
When browsing around on the Dark Web, it's important to be well informed of the potential risks.
Data Theft and Scams
The dark web is rife with scams, from fake product listings to phishing schemes that steal personal data. Unverified marketplaces may also sell counterfeit items or use false advertising. Proceed with caution and a healthy dose of skepticism while navigating the dark web.
In 2019, 620 million records were leaked or stolen from various companies including Dubsmash, MyFitnessPal and MyHeritage, and were later found for sale on the dark web. Stolen data often includes financial information, medical records, and social security numbers, which are used in identity theft and fraud schemes.
“Data theft is the currency of the dark web. Each breach and scam fuels an underground economy where privacy is no longer protected but sold to the highest bidder.” Brian Krebs, Cybersecurity Expert
Malware and Cybersecurity Threats
Due to the lack of oversight, the dark web is notorious for hosting malicious software and distributing it through various channels. A 2020 study found that more than 60% of dark web listings related to malware were tied to ransomware, Trojans, and other forms of cyber threats.
Emotet is a malware originally created as a banking Trojan that spread widely via phishing emails. It evolved into a service sold on the dark web, allowing other cybercriminals to use it for distributing ransomware and spyware. Emotet’s modular structure made it highly adaptable, infecting systems worldwide and causing significant financial damage.
It was dismantled in early 2021 by a global law enforcement effort, but it remains a notable example of malware distributed and purchased on the dark web for large-scale attacks.
Law Enforcement Monitoring
Law enforcement agencies worldwide monitor the dark web for illegal activities, such as the trafficking of illegal drugs, weapons, and stolen data. Interpol, the FBI, and Europol all have dedicated cyber units focused on dark web surveillance, often leading to high-profile arrests and marketplace shutdowns. In 2020 alone, Europol’s Operation DisrupTor led to 179 arrests globally and the seizure of $6.5 million in cash and cryptocurrency.
"The dark web may feel like the wild west, but it is not beyond the reach of law enforcement. We will continue to track those who believe they can evade justice by hiding online." - Christopher Wray, FBI Director
How to Check if Your Information is on the Dark Web
You may be wondering if your personal information has been compromised and if it's floating around on the dark web. Read on to find out what type of data is often stolen and how to check if your personal information is available on the dark web.
Data Breaches and Identity Theft
The dark web is a primary destination for stolen personal data from large-scale data breaches. When companies experience breaches, data like social security numbers, credit card information, account passwords, medical records, and even tax information often end up for sale on dark web marketplaces.
Cybercriminals use this data to commit identity theft, fraud, and other malicious activities. Notable breaches, such as those affecting Equifax, LinkedIn, and Marriott, exposed millions of users’ information, which quickly circulated on the dark web. This stolen data can be sold multiple times, leading to a lasting impact on victims who may face issues with unauthorized financial transactions, medical identity theft, or even criminal impersonation.
Tools to Monitor Dark Web Activity
Several tools monitor the dark web for stolen information to help individuals and businesses detect if their data has been compromised. Have I Been Pwned is a free service where users can check if their email address or phone number was exposed in a known data breach.
For more comprehensive, real-time monitoring, paid services like Experian Dark Web Scan, LifeLock, and Identity Guard offer ongoing alerts if personal data appears in dark web listings. These services scan dark web forums, black markets, and databases for personal identifiers such as emails, passwords, financial data, and even medical IDs, allowing users to take preventive action quickly if a match is detected.
These monitoring tools can be a valuable part of a personal or organizational cybersecurity strategy, alerting users to potential risks and helping them to secure accounts before further damage occurs.
Tips for Safely Navigating the Dark Web
Many of these tips are essential for all levels of the web: surface, deep and dark. You should always keep them in mind when online.
Essential Safety Tips
When navigating the dark web, safety and caution are paramount due to the risks of malware, phishing, and fraudulent sites:
- Tip 1: Always use trusted directories or search engines designed for the dark web, such as The Hidden Wiki or DuckDuckGo on Tor, to help ensure you’re accessing legitimate sites.
- Tip 2: Avoid clicking on unverified links or downloading files, as many sites harbor malicious software that can compromise your device’s security.
- Tip 3: Additionally, avoid sharing any personal information, including email addresses or phone numbers, as even seemingly small details can be used for identity theft or targeted phishing scams.
Using a VPN on the Dark Web
Did you know you can use a VPN on the dark web? A VPN adds an essential layer of security when accessing the dark web. By encrypting your internet connection and masking your IP address, a VPN prevents your ISP or other third parties from tracking your online activity. This is particularly useful for dark web browsing, as it provides an added layer of anonymity and protection. When combined with Tor, for example, a VPN can help prevent IP leaks and make it more difficult for network operators to trace your activities.
Recommended Security Measures
For the safest experience always use a reliable firewall, and multi-factor authentication (MFA). A reliable firewall helps block unwanted traffic and prevents unauthorized access to your device. Additionally, MFA for any accounts or services you use can be invaluable, as it adds an extra layer of protection even if your credentials are compromised. For best practices, update your security software regularly, and consider using endpoint protection to detect and block any potential malware that could compromise your system while browsing the dark web.
Conclusion
You must have realized by now that the dark web is a complex and often misunderstood segment of the internet. While it does host some illegal activities, it also provides a platform for secure communication and privacy protection, especially to those who most need it.
“The dark web isn't just about illegal activity; it's where people go when they need a place to speak freely without fear of repression. Privacy should never be a privilege, but a right.” - Eva Galperin, Director of Cybersecurity at the Electronic Frontier Foundation (EFF)
Like any platform, when navigating the dark web, it’s essential to stay informed, use reliable security tools, and proceed with caution. For those interested in exploring this hidden layer, understanding its risks and benefits is crucial for a safe experience.










