The main difference between Tor and a VPN is how your data gets routed: Tor uses a multi-layer connection method, while VPNs create a secure connection to a single server of your choosing.
Both are effective but different tools you can use to enhance privacy and security online. Which one you should use is entirely dependent on your use case, so let's explore each to understand which tool might be best for your needs.
Tor vs. VPN: What's Best For You?
What is Tor?
Tor is a term that gets used for a couple different things. When people say Tor, they’re probably referring to Tor Browser, which is the specific browser used to connect to the Tor Network, which is managed by the Tor Project.
Tor is short for "The Onion Router," and is free, open-source software that helps people worldwide browse the internet anonymously by routing data through a series of volunteer-operated servers, known as relays or nodes.
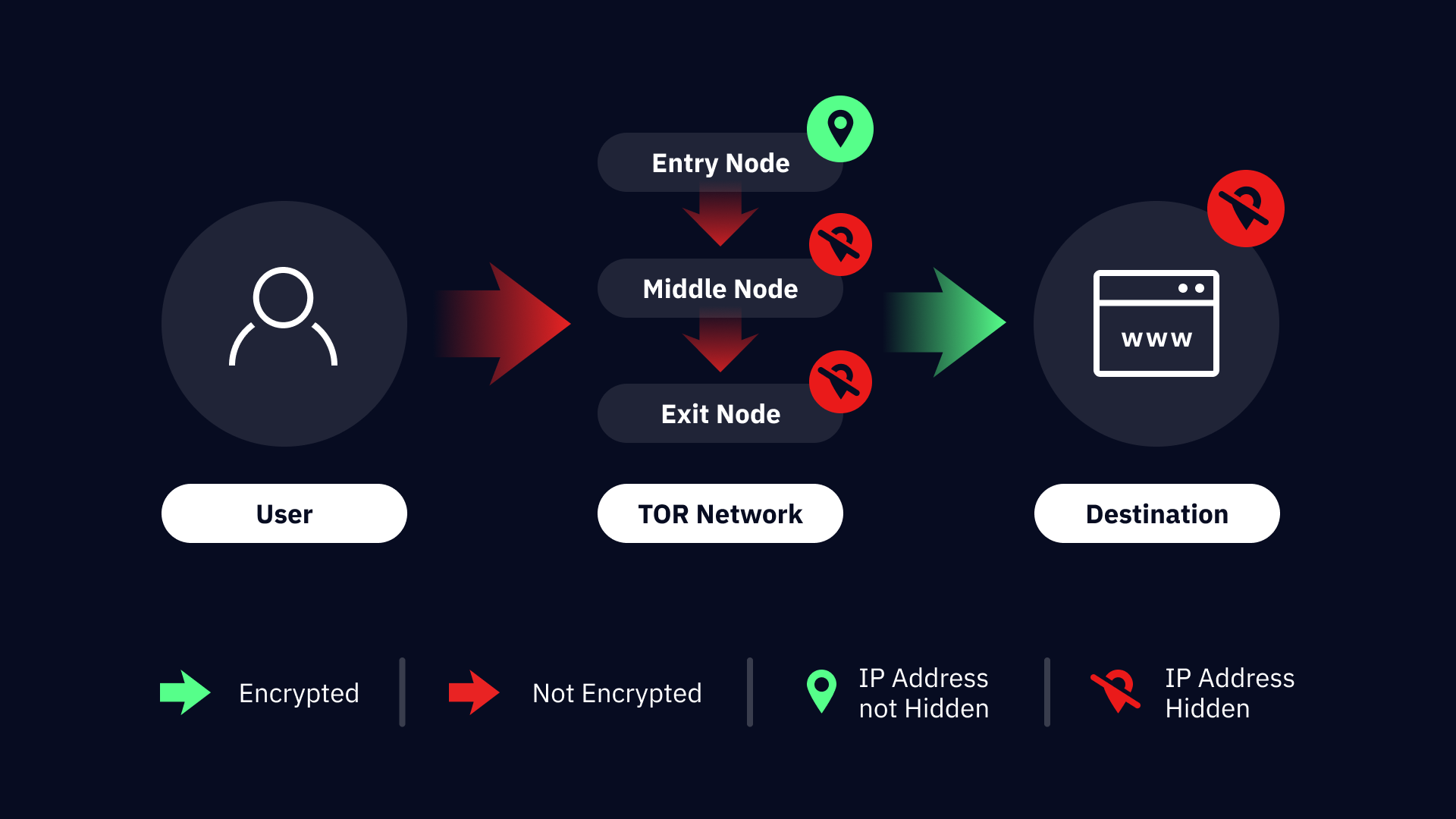
When you connect to Tor, each piece of your data is wrapped in layers of encryption, like an onion, and travels through several nodes before reaching its destination. This process ensures that no single point on the path knows both the sender and the recipient of the data, providing higher anonymity than other conventional methods. Here’s how Tor routes your data once connected:
Entry node: This is the first server you connect to. Your IP address can be seen because you initiate the connection from your device.
Middle (relay) node: The middle node acts as an intermediary between the entry and exit nodes. By adding a buffer layer, you can be sure that the exit node does not know the source (entry node) of the traffic, adding an extra layer of anonymity.
Exit node: The exit node is the final step, where your data reaches its destination. The destination website can be seen but doesn’t know your identity due to the middle node’s buffer layer.
Tor's multi-layered encryption approach and random routing system can be significantly slower than browsing the standard web. It’s ideal for activities where privacy is crucial, such as whistleblowing or accessing censored information. However, it's really not suited for bandwidth-intensive tasks like streaming or gaming.
Tor Pros and Cons
For those considering using Tor to achieve online anonymity, it’s important to consider online the pros and cons of using it over a VPN or other privacy preserving methods.
Pros: Free to use, great for circumventing censorship anonymously, fairly easy to use
Cons: Slow connections, not suitable for many use cases, requires trust in exit node operators
What is a VPN?
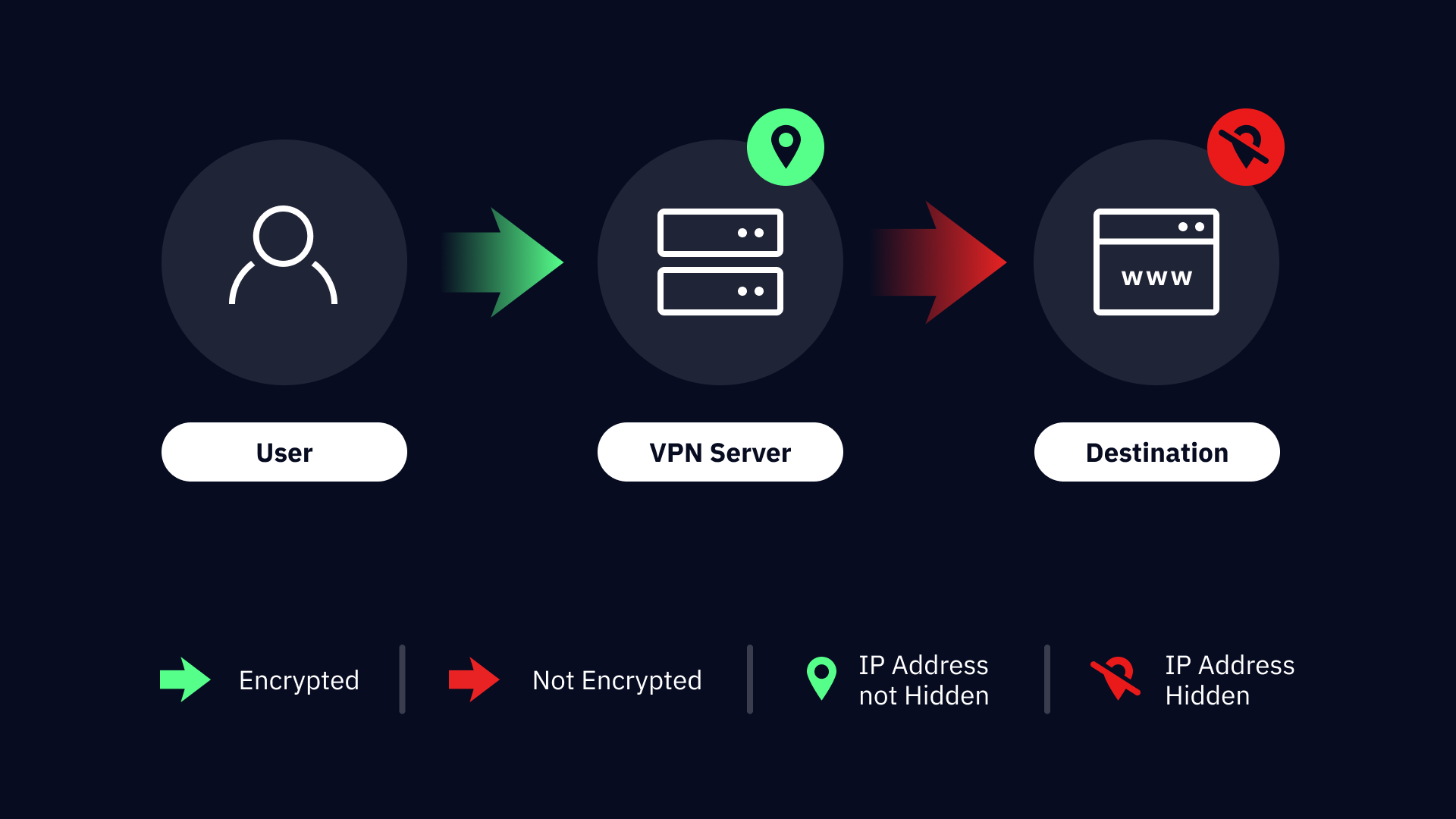
A VPN, or Virtual Private Network, provides a secure tunnel for your internet traffic via an encrypted connection established between your device and a remote server managed by a VPN provider like Windscribe. Connection to this server conceals your actual IP address and can be located anywhere globally, helping skirt geo-restrictions and enhancing online security.
Here’s how VPN connections work once you click that connect button:
- Establish secure connection: The VPN on your device creates a secure encrypted tunnel to the remote server, using a modern and secure VPN protocols like Wireguard
- Data Packet Encryption: After establishing a secure tunnel, your data will be encrypted before being transmitted. This step is vital, as it makes it impossible to for prying eyes like hackers, governments, or ISPs to intercept and read your data
- VPN Server Routing: Once the data is encrypted, it’s routed through the VPN server. The VPN server acts as a proxy (or a buffer) between your device and the websites you’re surfing. The websites can only see the IP address and location of the VPN server you’re connected to, adding a layer of anonymity to your online activities.
- Hiding among the many: You’re probably not the only one connected to the VPN server at any one time either. This means that you’re sharing the VPN server’s IP address with all those other connected devices, which obscures your true identity and enhances your online privacy.
VPNs like Windscribe offer faster connection speeds compared to Tor, making them suitable for everyday online activities like browsing, downloading, and streaming. Another perk of a paid VPN service is reliability and security. VPNs have an element of accountability since the server operators are professionals whose identity is known, contrasting with the decentralized Tor network run by volunteers.
Using a paid VPN service usually means you gain access to a larger number of privacy and security tools that Tor doesn’t offer. Some Windscribe specific examples include:
VPN Pros and Cons
For those considering a VPN over Tor as their privacy tool of choice, it’s imperative that they understand the difference between the two technologies, as well as the benefits and drawbacks each offers. For VPNs, here are the pros and cons:
Pros: Fast and reliable speeds, world wide connection options, additional security features
Cons: Centralized organization, reliable services are often paid tier, banned in certain countries
Is Tor a VPN?
No, Tor itself is not a VPN, but the underlying technology functions in a similar manner. Tor will only encrypt the data passed through the Tor browser, while a VPN like Windscribe will encrypt your entire device.
How do I use Tor Network?
In order to even access the Tor network, you need to use the Tor Browser, which is an optimized version of the Firefox browser for anonymity and privacy. Tor Browser is specifically designed to avoid browser fingerprinting, usually at the cost of your network speed due to multi-layer routing.
Will Tor make me anonymous?
It depends. Tor runs your data through several layers of encryption at once, while VPN providers usually only use one layer. However, because Tor only encrypts the traffic that goes through the browser itself, it’s only more anonymous with browser queries, while other apps on your device are left unprotected.
Does the Tor browser hide your IP address?
Yes, Tor hides your IP when you are using Tor browser. It’s important to note, though, that this only applies to the browser itself. Any other traffic that does not go through Tor will be exposed, unless you’re also using a VPN to route any non-Tor internet traffic.
Do I need to use a VPN with Tor?
It’s possible to use both Tor and VPN together, but there is really only one recommended way to do so. As mentioned above, the entry node for the Tor network can see your IP address. By first connecting to a VPN, you can obscure your real IP address from the entry node, adding an additional layer of security and anonymity.
While it provides a high degree of anonymity, this method will generally result in slower connection speed. You need to route your data through 4 servers: VPN server, Entry node, Relay node, and Exit node.
Connecting to Tor then a VPN is generally not recommended as it offers less anonymity than first connecting to the VPN, and will also slow down your internet connection as you are routing data via four servers: Entry node, Relay node, Exit node, and then the VPN server. Generally speaking, using only a VPN is generally enough for everyday use and will offer much faster speed compared to Tor.
Is a VPN Better Than Tor?
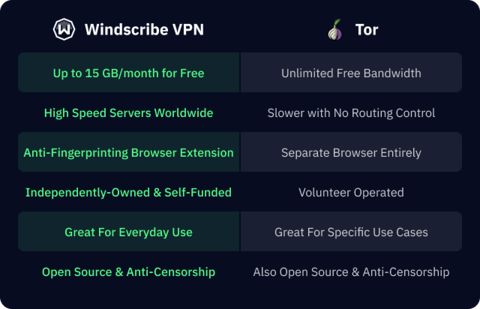
Both Tor and VPNs are powerful privacy tools but in different ways. Tor excels in providing anonymity through its three-node layering system, but it relies on the trustworthiness of volunteer exit nodes, which might be operated by law enforcement or unscrupulous individuals. Using Tor with a trustworthy VPN like Windscribe can mitigate some of these risks by encrypting your data before it even enters the Tor network, adding an extra layer of security.
VPNs, on the other hand, offer consistent encryption for all traffic leaving your device and advantageous speed capabilities, but they centralize trust in a single service provider. It’s imperative to find one that has a strict no-logs policy.
Is using Tor Legal?
It’s completely legal to use Tor and there are plenty of legitimate reasons to do so. Some examples of Tor usage where users would benefit from full anonymity and secure communication channels are whistleblowers, journalists, activists, and political dissidents.
It’s important to consider, while it’s legal to use Tor, it is not legal to conduct illegal activities whether or not they take place on the Tor network. Your online actions will be subject to your country’s laws and it's on you to make sure you aren’t putting a target on your back.
Is using Tor Safe?
Generally speaking it’s safe to use Tor, but using it comes with its own unique set of risks. Things you should be aware of while using Tor include:
- Exit Node Scams: As the final step in the multi-layer connection, design of the exit node offers an unfortunate opportunity for bad actors to exploit. Your connection needs to be decrypted by the exit node in order to complete your journey to whatever website you’re visiting.
It’s hypothetically possible for a malicious actor operating an exit node to see your unencrypted traffic and/or browsing activities. Therefore, it’s imperative that you ensure to only connect to websites with a valid HTTPS encryption, alongside using a VPN prior to initiating your Tor connection to further protect yourself.
- Malware & Phishing: Using Tor to access dark web sites for downloadable content is highly risky and inadvisable. Avoid clicking on or downloading any files that you come across on an onion site.
You should also exercise extreme caution when inputting personal information on any onion site. Your resources for protecting yourself from phishing on the dark web are very limited, so only give personal information to websites you trust.
- Traffic Pattern Identification: If you’re a frequent Tor user, your repeated browsing patterns might make you identifiable to exit node operators.
How to Be Safe While Using Tor
If you are going to frequent the dark web and interact with the community there, you should take extra steps to protect yourself. Make sure to follow these three steps to stay safe while using Tor:
- Add a VPN on top: Using a VPN prior to initiating a connection to Tor results in increased privacy and anonymity.
- Don’t be dumb: It sounds obvious, but a little common sense goes a long way. Use safe browsing habits like avoiding suspicious plugins or downloads, and don’t go blabbing out identifiable information on any forum or community website.
- Be careful with your onion links: some websites may have malicious content, others may have nefarious intentions. Double check that you’re accessing a trust onion site before you attempt to connect to it.
Conclusion: Tor vs. VPN
Choosing between Tor and VPN largely depends on your online activities and privacy needs. If ultimate anonymity is your priority, such as when accessing the dark web or bypassing heavy censorship, Tor is a valuable tool. However, if you require a balanced solution offering privacy without sacrificing speed, and need to encrypt all your online activities, a VPN is the way to go.
For those who need enhanced privacy, using both simultaneously can offer synergistic benefits, although it will lead to a reduced speed compared to using just one of them. Consider the specific requirements and constraints of your use case before you decide.









