In a world where data tracking and online surveillance have become the norm, tools for preserving privacy have gained significant importance. One of the most popular solutions is Tor, short for The Onion Router. Known by many as the “dark web browser,” Tor is much more than just a browsing tool; it’s a complex privacy network designed to keep online activities private. This article dives into the History of Tor, What Tor Is, How Tor Works, and why Tor Remains Essential for Privacy and Digital Freedom.
The History of Tor and the Tor Project
The development of Tor began in the mid-1990s when the U.S. Naval Research Laboratory started experimenting with anonymity networks to protect government communications. Researchers Paul Syverson, Michael G. Reed, and David Goldschlag developed onion routing, a technique designed to conceal the origins and destinations of online communications by wrapping data in multiple layers of encryption. This technology was initially intended for secure intelligence operations and protecting government officials’ identities online.
In the early 2000s, the U.S. government released onion routing technology to the public domain to help maintain anonymity for not only government operatives but also journalists, human rights activists, and everyday internet users. In 2002, The Onion Routing Project, or Tor Project, was officially founded to advance and maintain this technology.
Founding of the Tor Project
In 2006, the Tor Project, Inc. was established as a nonprofit organization, receiving initial funding from the Electronic Frontier Foundation (EFF). This new nonprofit was dedicated to making Tor accessible to the public, prioritizing open-source development and transparency. The Tor Project’s mission was clear: to protect and advance privacy, freedom of expression, and unfettered access to information. Since then, the Tor Project has grown significantly, gaining support from various organizations, including Mozilla, the Ford Foundation, and even the U.S. State Department.
Today, the Tor Project is staffed by privacy and security experts, and it relies on a global community of volunteers who help operate the network. As of 2023, Tor serves millions of users worldwide, and its mission continues to evolve in response to growing concerns about online privacy, censorship, and surveillance.
"Tor allows people to protect their identities online. It's used by journalists, human rights defenders, and whistleblowers around the world." Roger Dingledine, Tor Project Co-Founder
How Does Tor Keep You Anonymous Online?
At the core of Tor’s functionality is a concept known as onion routing, designed to make online activities anonymous through multiple layers of encryption. Each layer “peels off” like an onion as data passes through various nodes, revealing the data only at the intended destination.
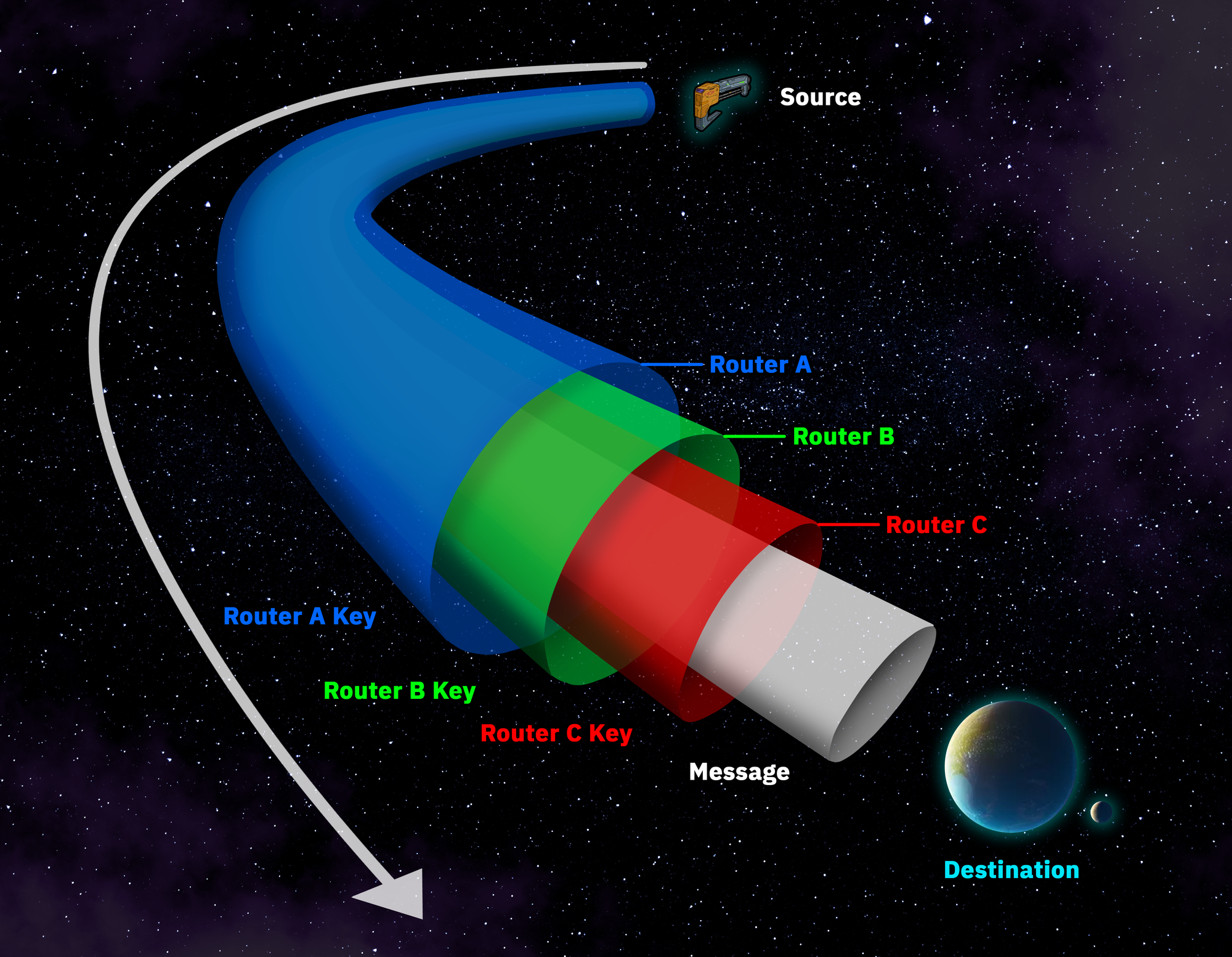
When you use Tor, your data is encrypted multiple times and passed through a series of nodes, each peeling back one layer of encryption. Only the final node—the exit node—sees the unencrypted data but doesn’t know the sender’s identity, making it extremely difficult to trace the data back to its origin.
What Are Entry, Relay, and Exit Nodes in Tor?
Tor’s privacy relies on its nodes, which are volunteer-operated servers in different parts of the world. These nodes are divided into three main types: entry, relay, and exit nodes.
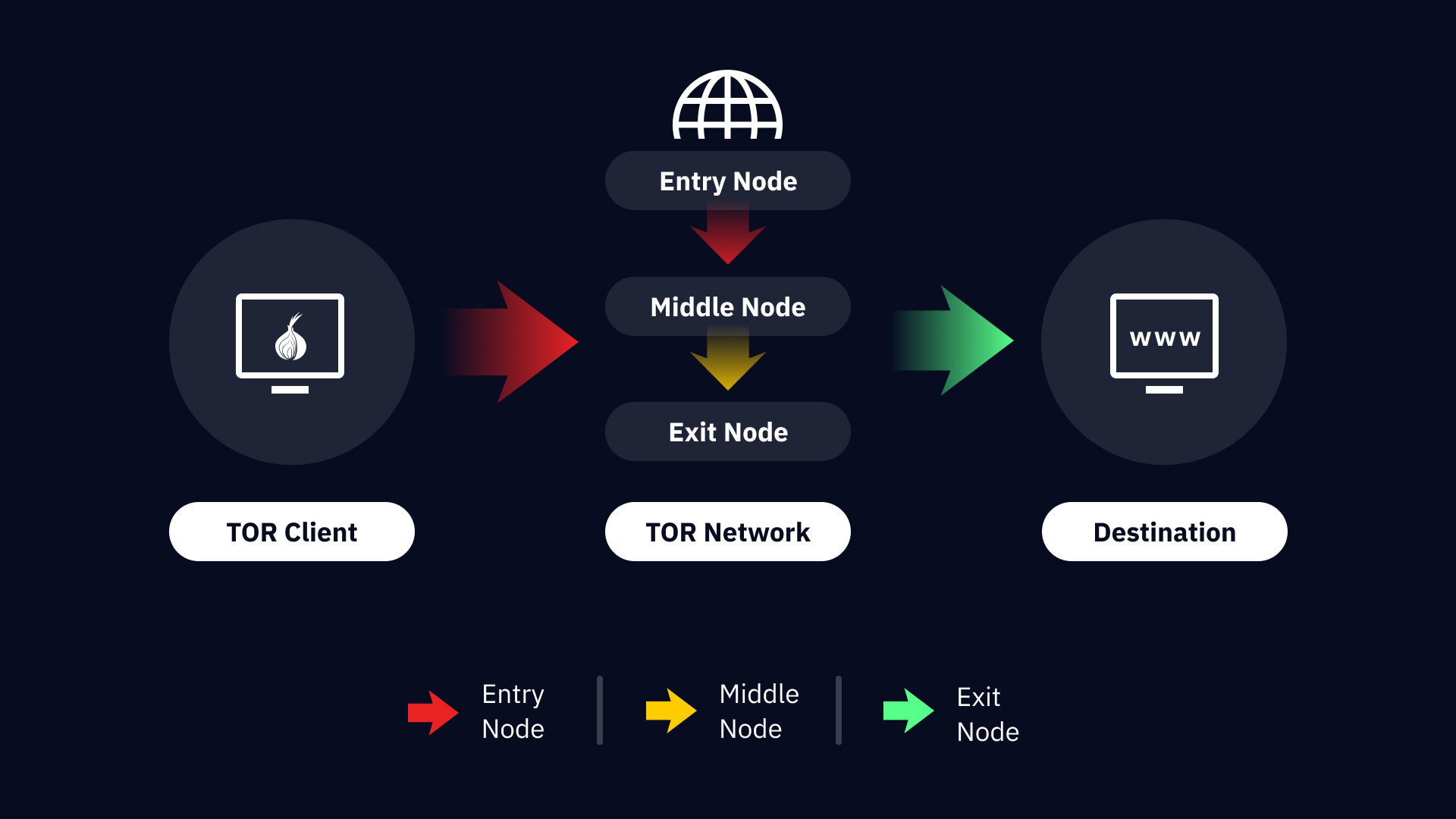
- Entry Node: The first point of contact in the Tor network. It hides the user’s IP address from the subsequent nodes, ensuring the user’s location is not visible.
- Relay Node: The middle node that forwards data to the next node. It only knows the previous and next nodes, preserving anonymity.
- Exit Node: The last node that transmits data to its final destination. Only the IP of the exit node is visible to the website being accessed, not the user’s original IP address.
The entire process takes milliseconds and renders it nearly impossible to determine both the user’s location and the destination site simultaneously.
Am I Completely Anonymous on Tor?
While Tor is one of the most robust anonymity tools available, it isn’t totally foolproof. There are potential weaknesses, especially if users visit unencrypted HTTP sites, where the exit node operator could intercept traffic. In 2013, documents leaked by former NSA contractor Edward Snowden revealed that the NSA targeted entry and exit nodes to identify Tor users. Though this approach requires extensive resources and is difficult to execute, it’s a reminder that Tor is not entirely invulnerable.
What is the Tor Browser, and How Does it Work?
The Tor Browser is a customized version of Mozilla Firefox that allows easy access to the Tor network. It includes built-in privacy features like blocking third-party cookies, preventing tracking scripts, and offering default access to .onion sites, which are part of the hidden web only accessible through Tor.
- Accessing .onion Sites: The Tor Browser provides access to .onion sites, which are not accessible through regular web browsers. Examples of legitimate .onion sites include SecureDrop, a tool used by media organizations to receive secure, anonymous tips from sources. Major media outlets like The Guardian and The Washington Post use SecureDrop to protect their sources.
- Enhanced Privacy Features: The browser blocks ads, disables plugins that can leak your identity, and has NoScript enabled by default to prevent tracking scripts.
What Other Apps and Operating Systems Use Tor for Privacy?
Beyond the Tor Browser, several applications integrate Tor to offer users more privacy. Here are three popular tools:
- Orbot: A mobile application for Android devices that routes all internet traffic through Tor, providing secure browsing and app usage.
- Tails OS: The Amnesic Incognito Live System (Tails) is a live operating system that users can boot from a USB drive. It routes all network traffic through Tor and leaves no trace on the host computer, making it a favorite among privacy advocates and journalists.
- OnionShare: An open-source tool that allows users to share files, host websites, and chat securely over the Tor network.
Some other apps and operating systems that use Tor are: Ricochet Refresh, Briar and Who.
In a 2013 report from Access Now, a digital rights advocacy group, a Syrian activist shared:
The government’s crackdown on internet usage meant we had to use tools like Tor. Without it, we wouldn't have been able to get information out safely."
– Source: Access Now, Case Studies in Online Anonymity
What is Tor Actually Used For?
Tor is absolutely essential for life-critical privacy and freedom of information. If you have had to consider the importance of your online privacy or access to information, consider yourself lucky. Let’s take a look at what Tor is actually used for in a little more detail.
How Tor Protects Privacy and Prevents Tracking
One of Tor’s primary purposes is to prevent tracking and protect user privacy. By hiding IP addresses, Tor stops websites, advertisers, and internet service providers (ISPs) from tracking browsing activity. This feature is particularly valuable in regions where surveillance is common.
In Belarus, during the 2020 protests against President Alexander Lukashenko, the government imposed internet restrictions. In response, Tor usage surged by over 300%, as people relied on it to access uncensored news and communicate with the outside world.
Using Tor to Bypass Censorship in Restricted Countries
Tor is widely used in countries with strict internet censorship to access information that is otherwise blocked. For example, in China, where the “Great Firewall” restricts access to major platforms like Google, Facebook, and YouTube, people use Tor to bypass these restrictions.
Why Journalists, Activists, and Whistleblowers Rely on Tor
For journalists and whistleblowers, Tor provides a secure means to share information and communicate without fear of government surveillance. Tor is often combined with secure messaging and file-sharing tools, ensuring a high level of anonymity.
How Tor is Used to Access the Dark Web
Tor’s reputation is often linked to the dark web, the hidden part of the internet only accessible via Tor. While the dark web has legitimate uses, such as private forums and whistleblowing sites, it’s also known for illicit marketplaces and illegal activities.
How Safe and Secure is Tor? Pros and Cons of Using Tor for Privacy and Anti-Censorship
When considering Tor, you must consider the pros and cons, as with any tool or software.
Pros of Using Tor
- True Anonymity: Tor’s use of multiple relays ensures that the user’s IP address is concealed, making it difficult to trace browsing activities.
- Access to Censored Information: Tor enables users to bypass censorship and access restricted information, which is particularly valuable for those living under repressive regimes.
- Essential for Privacy Advocates: For activists and individuals who need strong privacy, Tor provides a level of security that traditional browsers can’t match.
Cons of Using Tor
- Potential for Exit Node Monitoring: While data is encrypted throughout its journey, it becomes vulnerable at the exit node. Unscrupulous exit node operators could, theoretically, intercept unencrypted data, although this remains rare.
- Slower Speeds: Due to multiple relay nodes, Tor can be slower than traditional internet connections. For high-speed activities, such as streaming, it’s often impractical.
- Not Foolproof: Using Tor doesn’t guarantee complete anonymity, as websites can still track some browser behavior. Combining Tor with HTTPS is recommended for added security.
Is Tor Secure for Private Browsing?
Tor offers a high level of privacy, but combining it with other tools, like a VPN, can increase security. Some users connect to a VPN before accessing Tor to protect against ISP monitoring, although this may slow down connection speeds.
Is Tor Legal? Legal and Ethical Considerations of Using Tor
In most countries, using Tor is legal. However, certain governments restrict Tor because of its potential to bypass censorship. China and Russia, for instance, have attempted to block Tor altogether, labeling it a threat to national security.
Why Do Some Countries Block or Ban Tor?
Governments that restrict freedom of speech or limit access to information may view Tor as a threat, since it allows users to access blocked content and communicate anonymously. Blocking Tor is a way for these governments to control information flow and monitor dissent.
Tor’s anonymity makes it an attractive tool for criminal activities on the dark web. This dual-use nature raises ethical questions: while Tor protects privacy, it also enables illegal activities. Governments and privacy advocates have debated how to balance Tor’s benefits with its potential risks.
Should I Use Tor or a VPN? Comparing Tor with VPNs and Other Privacy Tools
Both Tor and Virtual Private Networks (VPNs) help anonymize data, but they function differently. A VPN routes traffic through a single server, masking the user’s IP but not offering complete anonymity. Tor, on the other hand, uses multiple relays, making it more secure for anonymity but slower. For more on the topic, check out our article: Tor vs VPN.
Can You Use Tor and VPN Together?
Yes, combining Tor with a VPN can offer additional protection. For instance, connecting to a VPN before Tor hides Tor usage from the ISP, while connecting to Tor before a VPN conceals your VPN traffic from Tor exit nodes. However, this combination may slow down the connection.
Many journalists in highly censored countries use a VPN-Tor combination to ensure anonymity and access censored websites without drawing attention.
What’s Next for Tor? Future Innovations and Challenges for the Tor Network
Tor continues to improve its performance with new technologies. For instance, Arti, a Rust-based implementation of Tor, is designed to make the network faster and more resilient to censorship.
Will New De-Anonymization Techniques Impact Tor’s Effectiveness?
Advanced de-anonymization techniques, such as traffic analysis, pose a challenge for Tor. However, the Tor Project is constantly working on solutions to counteract these threats and maintain privacy.
How to Support the Tor Project and Keep Privacy Tools Available
The Tor Project relies on community support. Donations from organizations like Mozilla and Electronic Frontier Foundation help fund the development of privacy tools and keep Tor accessible.
Conclusion: Should You Use Tor for Private Browsing and Security?
Tor is a powerful tool for those seeking privacy and access to uncensored information. Whether you’re a journalist, activist, or simply a privacy-conscious individual, Tor can provide an extra layer of security. However, it is essential to understand its limitations and use it responsibly. By combining Tor with other privacy tools and following best practices, users can navigate the internet more safely and freely.










