This is a technical article that will dive into the details of DNS, how it works, the different types of DNS and how Windscribe makes it possible for you to be the master of.... DNS. Yeah, we're gonna say DNS a lot.
Grab a fruit rollup, your favorite brand of chewing tobacco and a glass of the finest whiskey you can find, and let's dive in.
WTF is DNS?
Unlike humans, the computers that you use every day don't actually speak English (or any human language). In the world of networking (the system that connects two or more computers together), the same rules apply.
In order for a connection to be established between two computers, they both require an IP address. These addresses may look a little something like this: 147.185.34.1. Or this 2606:1a40:3::1. Every time you type in a URL into your browser, or click a link, you will end up connecting to an IP associated with that URL. Then you will request data, like an image, a video, an HTML page filled with content, etc. Imagine having to remember random sequences of numbers to reach your favorite websites, instead of a domain name - it would make using the internet quite annoying.
This is where DNS (Domain Name System) comes in. DNS maps human readable domain names, like controld.com, to IP addresses, which then return you the information on that website. However, IP addresses can change at anytime, so DNS allows for a static and memorable name to point to a set of IPs - so no matter how many times they change, you will always reach your destination if you remember the domain name.
Every internet-connected device uses some kind of DNS server. They can be configured directly on the device itself, or, more commonly, configured on an entire network (like your home WiFi). In most cases, you're likely using the default DNS server supplied by your Internet Service Provider. Unfortunately, your ISP stores every DNS query you make, which is how they capture your browsing history - which they can sometimes resell to marketers or show to law enforcement.
There are many types of DNS servers, including but not limited to:
- Root servers
- TLD servers
- Authoritative servers
- Recursive servers
- Forwarding servers
- Caching servers
In order not to bore you out of your mind, I'm going to skip explaining most of these and just focus on the ones you're most likely to encounter, which are Recursive and Forwarding DNS servers. Both of these will be important later.
Recursive DNS Server
These DNS servers perform DNS lookups against authoritative, TLD and root servers. So when you type in "windscribe.com" the following things happen:
- Ask root server: "Where is com?" This in turn delegates to a TLD server.
- Ask TLD server: "where is windscribe?" This in turn delegates to an Authoritative DNS server.
- Ask Authoritative server: "What are the IPs for windscribe.com?" and you get an answer.
At this point your browser will establish a connection to those IPs and download the Windscribe homepage. Examples of cloud based recursive DNS servers include:
- Control D
- Cloudflare
- Google DNS
- Quad9
Non-cloud based DNS servers capable of recursive lookups include BIND and PowerDNS.
Forwarding DNS Server
A forwarding DNS server is a lazy DNS server, it doesn't do any of the above, and just asks a Recursive DNS server for the answer, which does all the work. Kinda like that one guy in your school group project.
As you may realize, that means DNS queries go to a 3rd party in order to actually be resolved. That 3rd party likely keeps logs.
DNS Protocols
There is another thing we need to talk about before we continue: DNS protocols. You may be familiar with "Legacy DNS" which, as the name suggests, is an ancient DNS protocol dating back to 1980s. These DNS servers usually come in a form of a pair of IP addresses, like 1.1.1.1, or 8.8.8.8, but there are several other, more modern protocols now, so let's discuss them...
Legacy DNS
The OG protocol. It's been around for 40+ years, and is supported by every Internet connected device. The downside is that it's not encrypted and is easily interceptable and spoofable. This means a "bad entity" (your ISP, network admin, your mom) who owns your network can see what websites you visit, and can craft fake responses to your DNS queries, which use a unique protocol and port: UDP 53.
DNS-over-HTTPS (DoH)
This is a modern DNS protocol that leverages TLS - the same thing that encrypts every single https:// website you visit. But instead of getting a webpage, you get a DNS record. This protocol is quite nice because its indistinguishable from normal browsing activity, as it operates over TCP 443 and UDP 443 (DoH3). Since its encrypted with TLS, an outside observer cannot see which domains you're requesting, nor can they spoof (fake) the answer.
DNS-over-HTTPS has 3 major versions, 1, 2, and... drum roll please.... 3, which mirror HTTP protocol versions.
This protocol is supported by all modern browsers and operating systems, except Android. However upcoming versions of Android will support DNS-over-HTTPS version 3.
DNS-over-TLS (DoT)
This DNS protocol is similar to DNS-over-HTTPS, since its also encrypted with TLS (its literally in the name) but does not have the overhead of HTTP. This makes it hypothetically faster than DNS-over-HTTPS, but in the real world it does not matter since the difference is measured in micro-seconds. It has one major flaw: much like Legacy DNS, it operates on a unique port, TCP 853, which makes it trivial to detect and block. An outside observer cannot see the queries themselves, or spoof them, but can easily prevent you from using this protocol. Many cellular providers world wide block this protocol outright.
This protocol is supported by most operating systems, like Android, iOS, MacOS and Linux (with some extra steps).
DNS-over-QUIC (DoQ)
This DNS protocol is similar to DNS-over-TLS, except it uses UDP as transports instead of TCP. This, in theory, makes it faster than DoT, but it suffers from the same flaws: it operates on a unique port, UDP 853, which makes it trivial to detect and block.
You are unlikely to encounter this protocol, as its not natively supported by any OS or device. DNS-over-HTTPS/3 combines the best of both worlds: DoH (hard to block) and DoQ (high performance).
Windscribe DNS (R.O.B.E.R.T)
When you use Windscribe, the VPN server you're connected to also becomes your DNS server. What kind of DNS server you may ask? Recursive of course. Every Windscribe server performs a full recursive DNS lookup for every DNS query you generate while connected to Windscribe, this means your DNS queries don't get transmitted to any 3rd party.
The Windscribe DNS server is only available over a local IP address, which is not publicly routable on the Internet. This means you must be connected to Windscribe in order to use it. This, combined with a paranoid level Firewall that's part of all our apps, blocks all external DNS resolutions and ensures that your DNS queries cannot leak to any 3rd party, or get intercepted and spoofed.
In most cases, this is exactly what you want. However, if you're reading this blog post, you're special and "most cases" don't apply to you. Or maybe you just want to learn more? Well, you've come to the right place.
Custom DNS
There may be cases when you wish to use your own DNS server, or that of a trusted 3rd party which could be classified as a "DNS leak" – but not all DNS leaks are bad, more on this later.
Self Hosted DNS
- Managing your DNS resolution gives you a great deal of control of your Internet experience. You may be operating a custom DNS server like Pi-Hole that you may wish to use alongside Windscribe, which offers best in class customizable DNS, we're not going to be sad if you choose not to use it, well, maybe a little sad.
3rd Party
- Despite Windscribe being a no-logging VPN, which doesn't log your DNS queries or sites you visit, you don't have to take our word for it. You may wish to send your DNS queries to another trusted DNS service like NextDNS, AdGuard, or even Control D (although that would be weird if you don't trust us... because it is us) using a Secure DNS protocol. This means we couldn't log your DNS queries, even if for some reason we wanted to. That way, you don't put all your "eggs" into one basket, which is a sound precaution.
When you use Custom DNS, you're "leaking" your DNS queries to a 3rd party (or yourself) which is not as bad as it sounds. In cases of a 3rd party DNS resolver, those queries still go over the tunnel, so your IP is masked from the 3rd party. In cases of a self-hosted solution, those queries would go to your local DNS resolver outside of the tunnel, but this don't reach the open Internet... unless you send them to a forwarding DNS resolver, which you probably will... so in that case you're totally leaking your DNS, in the worst way possible. As you see, this is very easy to get wrong.
How to (safely) use custom DNS
Windscribe is one of the few VPN providers who give you the ability to hide your DNS queries from us. It's not enough to just give you the ability to use Legacy DNS along with your VPN (which is pointless, since its not encrypted), Windscribe gives you the ability to use modern and secure DNS protocols that ARE encrypted, meaning we wouldn't know what you're up to, even if we went full evil. Well, technically there are other ways we can be evil like SNI filtering, and deep packet inspection, and there are solutions to that too, but let's keep things simple for now, shall we?
All Windscribe apps (mobile included) now support the ability to override the default Windscribe DNS server (R.O.B.E.R.T), which you can find in the Preferences -> Connection tab -> Connected DNS.
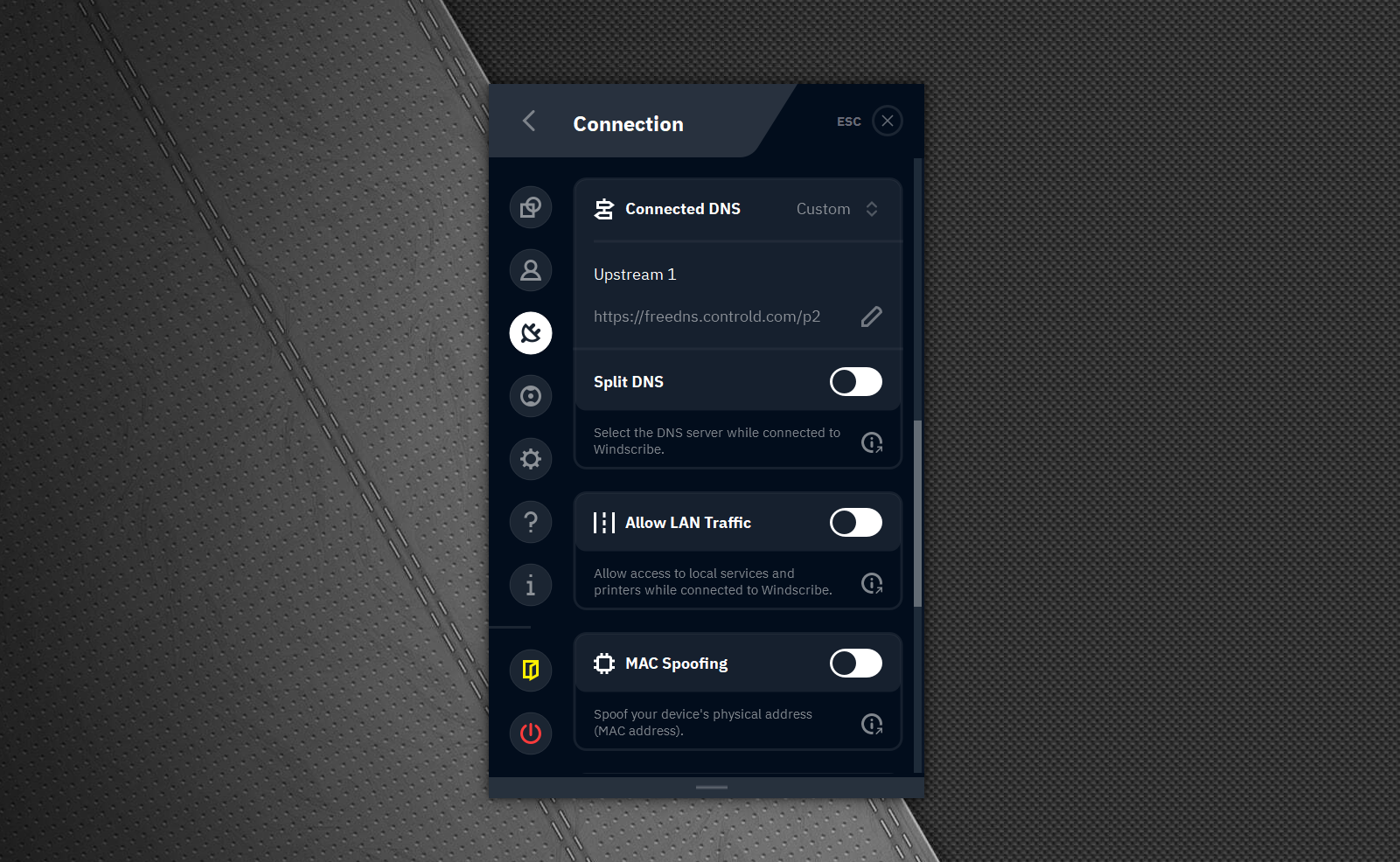
Here you can input any Legacy DNS, DNS-over-HTTPS, or DNS-over-TLS endpoint, and the Windscribe app will dutifully send your DNS queries to a 3rd party DNS server of your choice.
- Legacy DNS: Input the IP (ie.
76.76.2.2) - DNS-over-TLS: Input just the hostname (ie.
p2.freedns.controld.com) - DNS-over-HTTPS: input the full URL (ie.
https://dns.controld.com/12345) - QUIC based protocols (DoQ and DoH3) are currently not supported, but may be in the future.
The "fun" doesn't have to stop here, on desktop platforms you have the ability to use multiple DNS servers, and split route your DNS queries between them.
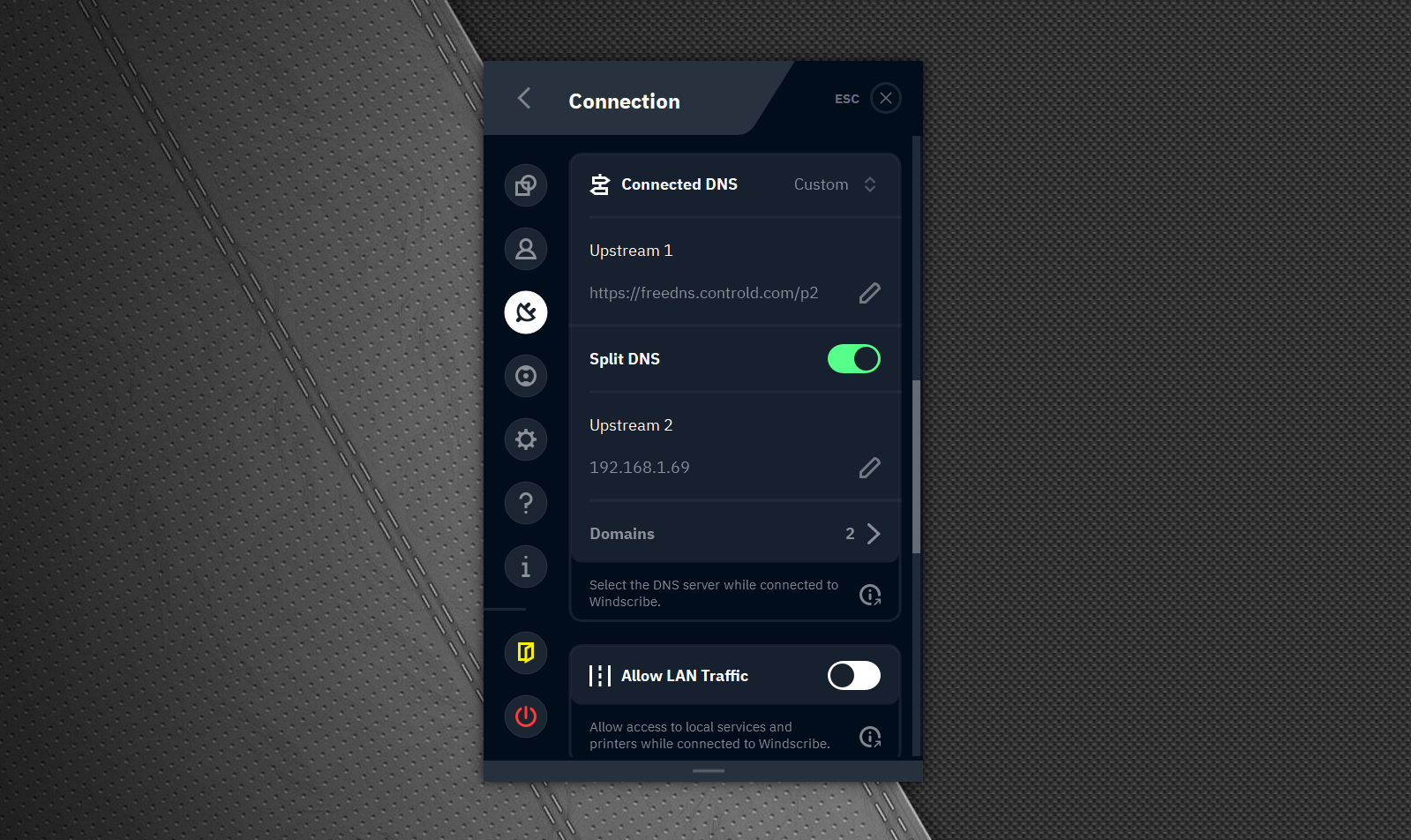
The above example provides a scenario where you operate your own (local) DNS server, that resolves your "special" domains that are not in public DNS. You would setup split DNS to send your special domains (wildcards are supported too) to your own DNS server (Upstream 2), while everything else uses the primary (Upstream 1).
This functionality is built directly into Windscribe, however if you're using a... puts on a top hat and monocle.... lesser VPN service that doesn't support this, use this handy open source project made by our sister company, Control D, that knows a thing or two about DNS. In fact, our own apps use this exact software under the hood. With this tool, you can achieve similar functionality with almost any other VPN. But seriously, just use Windscribe.
Control D + Windscribe
Are you looking to use Control D with Windscribe, while connected AND while disconnected? There is a way to do that as well.
- Install Control D's ctrld DNS daemon (you may already have it running if you did the Automatic Setup)
- In Preferences -> Connection -> Custom DNS, use
127.0.0.1as Upstream 1
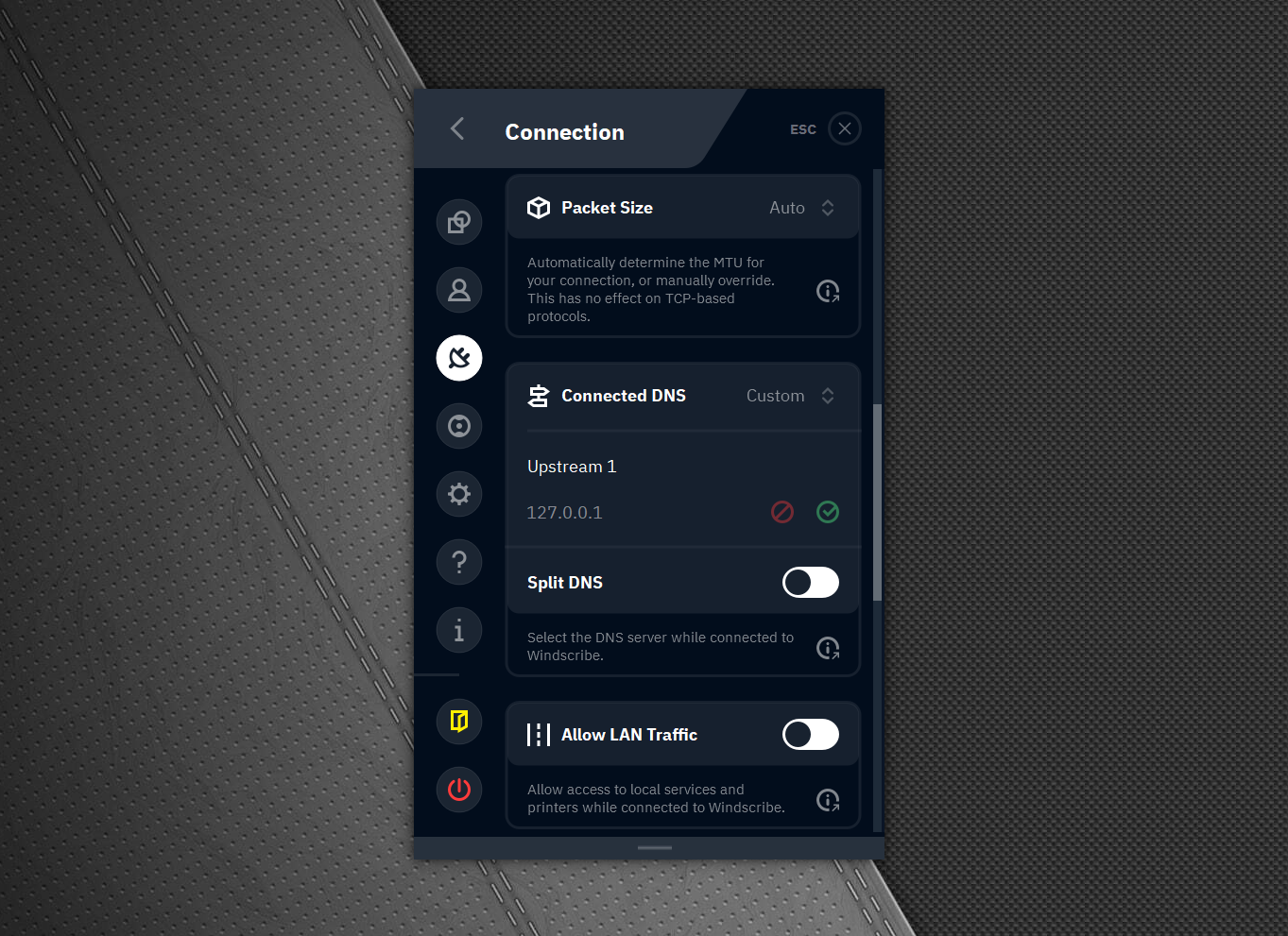
If this doesn't error out, you're done (if it errors out, you're not running ctrld). Now Windscribe will use the existing ctrld DNS server on your computer while connected.
Tell Me More
Well, I can, but I'm frankly surprised you made it all the way here. Kudos for not being a millennial/zoomer stereotype with the attention span of a fruit fly. For all the boomers out there, good on you too for not falling asleep. See, we offended everyone, equally.

I hope this helped shed some light on this mysterious DNS thing, and cleared up any misconceptions you may have had.










