It’s hard to really wrap your head around the staggering amount of digital information that is being produced on an average day. A recent study from Statista estimates that we generate a mind-blowing .33 zettabytes per day; this is equivalent to 328.77 million terabytes or 328.77 billion gigabytes.
Much of this data is transmitted via underwater cables that your everyday person is at best vaguely aware of. There are millions upon millions of kilometers of cabling in our oceans, run by governments that we’d argue don’t have people’s best interests at heart; to say there are privacy and security concerns would be putting it… Diplomatically (insert NCIS shades meme here).
To really understand this topic, however, I think it’s important to first take a look at the behavior of certain intelligence agencies.
The Snowden Revelations
For the context of this piece, I’m mostly going to focus on the Western World and their surveillance capabilities, largely because we have the most information about their practices and procedures. It would behoove one to assume that other adversarial (yeah, I said it, the US government ain’t getting no pass either) governments like China and Russia are also monitoring the world's data on a massive scale.
But the point at hand is known US/Western SIGINT alliances monitoring capabilities and technologies. If you’re curious to learn more specifics about how the sharing agreements of these US/Western SIGINT alliances work, we’ve already covered this topic in detail.
Let’s take a trip back to 2013 and a name that’s probably familiar to many of you: Edward Snowden. It is because of this man that we are aware of (some of) the surveillance capabilities of most Western governments. Among the numerous things we learned in the Snowden leaks, two of the most concerning revelations were the existence of programs called PRISM and XKeyScore.
As a general rule, PRISM involves data that is already stored, while XKeyScore involves the mining of data via (usually illegal) wiretapping or telecomms tapping. XKeyScore purports to provide the technical capability of monitoring essentially anyone the analyst wants to, regardless of legality or jurisdiction.
At this point, it’s safe to assume that the United States government is monitoring multiple points of critical internet infrastructure at any given time. Underwater submarine cables are no exception to this.
The Cables Carrying Your Data
You may be wondering, why should I care about some cables that live next to a pineapple under the sea (shoutout my fellow millennials)? Well, if the global system of communication we call the internet can be represented by a human body, these underwater cables are the nervous system. Generally shielded from the view of the public, these cables carry information to and from locations spread across the globe.
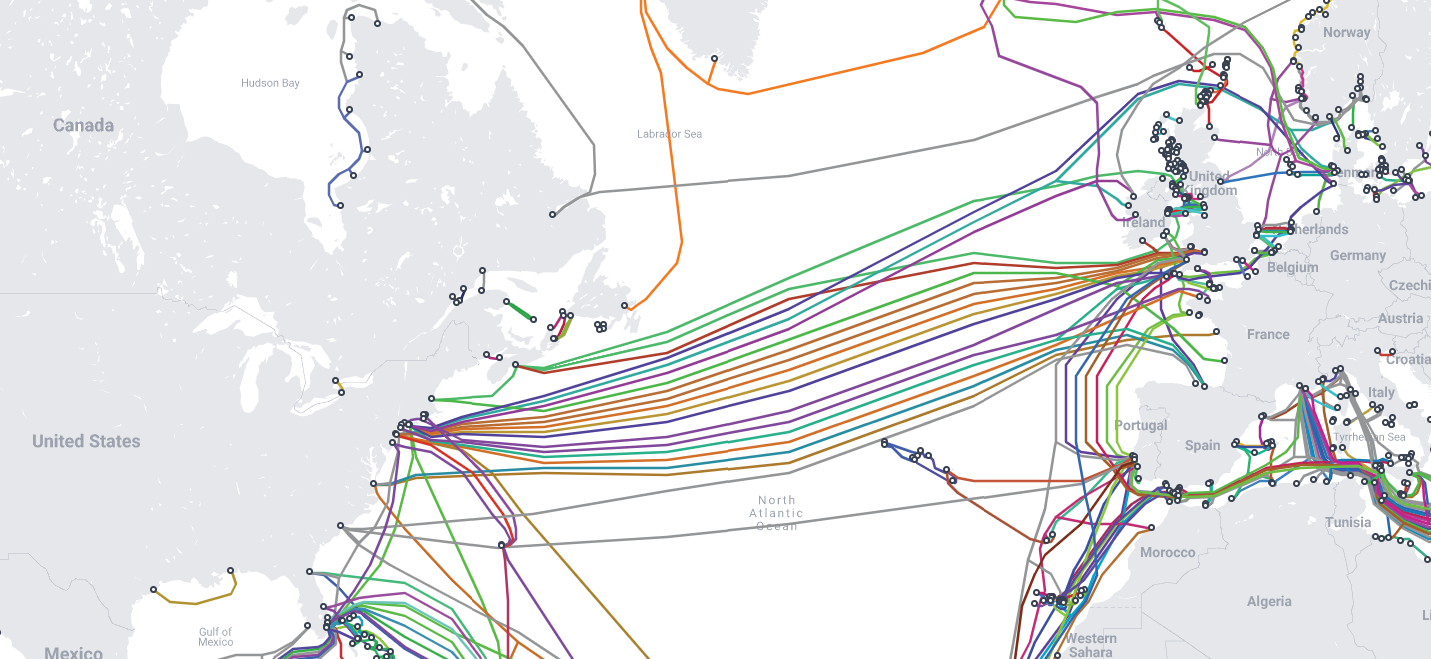
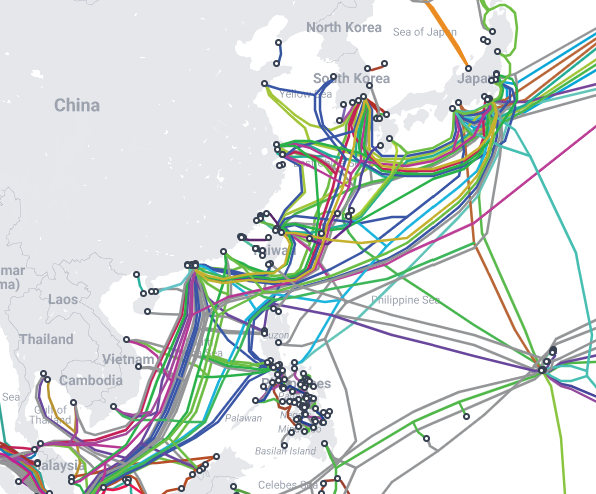
It’s hard to overstate the importance of these cables to modern society. We’re talking millions upon millions of kilometers of largely unguarded cables, carrying the communication signals that make our lives so convenient. Despite the added challenge of being completely underwater, sometimes thousands of meters below the surface, these cables are not impervious to sabotage or spying.
Unfortunately for you, dear reader, this is far from the only piece of the puzzle. Another important thing to take into account is that much of this surveillance is at best legally dubious, if not outright criminal. There are, however, legal mechanisms that enable this type of behavior at a large scale within the US intelligence community (and likely their bffs, looking at you Tony Blair).
Section 702
The legal mechanism that I’d like to highlight here is called Section 702. In a nutshell, Section 702 is a 2008 statute that legalized a warrantless surveillance program that started after 9/11. The key word there is warrantless.
The good news: Section 702 is due to expire this December. The bad news: the current administration and the entire US intelligence community are lobbying hard for this law to be extended another round. Their argument is that “it’s critical for gathering foreign intelligence and countering threats.”
Under its current interpretation, Section 702 allows the government to collect communications of targeted foreigners abroad, including when interacting with Americans, without a warrant on domestic soil. It permits the NSA to order companies like AT&T to intercept and hand over phone calls, texts, and internet communications to or from a foreign target. And if they can’t obtain it through “legal” means, they’ll just buy it from them. Yeah, you read that right.
Here’s a great timeline created by the EFF that demonstrates how the NSA started spying on everyone.
Let’s go over the facts at this point. The US government can ostensibly deduce your location and activities at any given moment, without any justification. They can do so through several different methods, both legal and illegal in nature, but equally comprehensive in scope. It’s safe to say that by extension, the governments of China and Russia likely have these sorts of technical capabilities, but until we have a Snowden-type whistleblower from either country my previous statement will remain theoretical.
A Recipe for Disaster
Now it’s time to digress back to the original point of this article, the underwater cables. It’s hard to overstate the importance of these cables in modern society. We are a society that is now entirely dependent on being interconnected to one another at any moment's notice. That type of dependence comes with a serious inherent risk: it’s entirely dependent on significant investment in developing the infrastructure, much of which is vulnerable to all sorts of tampering and tapping.
No authority governs the bottom of the ocean, nor does anyone have the capacity to monitor what is going on along the thousands upon thousands of kilometers of underwater cabling that carry the world's communication signals through them.
Ask yourself, do you trust the governments of the world not to exploit that? I’ll give you a clue: it’s already happened. If you want to read a story about cable tapping straight out of James Bond, I suggest you check out Operation Ivy Bells.
The dependence on and vulnerabilities of these underwater cables, coupled with the tendency for governments to justify whatever the hell they want, is a ticking time bomb.
Take Measures to Protect Yourself
Armed with billions of dollars at their disposal, access to incredibly large amounts of data, and a will to monitor everyone at every moment in time, Western Intelligence Agencies will continually ramp up their spying capabilities as technology advances. It’s safe to say that, even if you have nothing to hide, you are being watched anyway. There is no privacy super app or service that will help you circumvent mass surveillance.
True Privacy requires diligence and dedication. It’s no trivial matter to obfuscate your digital footprints. Simply having an existence online creates a limitless source of data for companies and governments to mine, exploit, and/or monetize. It’s not an exaggeration to say that personal data is as valuable a commodity as any precious metal or oil.
Using a VPN like Windscribe is part of a comprehensive strategy to keep yourself and your data safe online. The First 100 here can claim one of our cheapest annual plans, only $29 for a full year of Windscribe Pro.









