Whether you're a journalist, a privacy advocate, or just curious, this guide will walk you through how to access the dark web safely and responsibly.
Accessing the Dark Web with Tor Browser and VPN
Let’s start with the most common method: how to set up and use Tor Browser and a VPN to safely access the dark web.
Step 1: Install a VPN
The first is to download and install a reliable VPN. Choose a VPN known for strong encryption, a no-logs policy, and compatibility with various devices.
- Research VPN options: Look for a VPN with strong security features and a proven record of not keeping logs.
- Download and configure the VPN: Install the VPN app on your device and log in. If your VPN has multiple server locations, select one that’s neither in your home country nor geographically close to you. This further enhances your anonymity.
- Activate the VPN: Before you open Tor Browser, turn on the VPN to secure your internet connection.
Step 2: Download and Install Tor Browser
The first step is to install Tor Browser on your device. Make sure to do it safely from the official website:
- Visit the official Tor Project website: To ensure you download a genuine version, go directly to https://www.torproject.org. The site automatically detects your device type and provides the correct download link (e.g., for Windows, macOS, Linux, or Android).
- Install the browser: After downloading the installer file, follow the installation instructions specific to your device. Tor does not require complex setup, and it runs as a standalone browser, separate from your other internet activity.
- Configure Tor settings: On your first launch, Tor will ask if you’re in a country where access to the dark web is restricted. If yes, configure Tor bridges to bypass restrictions.
Step 3: Launch Tor Browser
With your VPN active and Tor installed, you’re now ready to connect.
- Open the Tor Browser: Locate the Tor Browser on your desktop or applications folder and launch it. You’ll notice that the browser has a unique design with a focus on privacy.
- Connect to the Tor network: Click “Connect” to start the process. Your internet traffic will route through multiple nodes, so it may take a few moments to establish a connection.
Step 4: Start Browsing the Dark Web
Once connected to Tor, you’re ready to begin exploring the dark web. However, keep in mind that the dark web is not organized like the regular internet. Instead of search engines, you’ll need to rely on directories or specific .onion links.
- Use a dark web directory: Directories like “The Hidden Wiki” list .onion sites across categories. This can be a great starting point, but be cautious, as these sites aren’t regulated and may include questionable content.
- Avoid suspicious sites: The dark web can host both harmless and harmful sites. Stick to reputable sources, such as forums, marketplaces, or resources that are widely known and vetted within the dark web community.
Accessing the Dark Web on Various Devices
The steps to access the dark web vary slightly depending on your device, but here’s a breakdown:
Accessing on Windows and Mac:
For Windows and Mac, the process is straightforward:
- Install both the VPN and Tor Browser.
- Enable the VPN and connect to a secure server.
- Open Tor Browser and connect to the Tor network. Once connected, you’re ready to browse .onion sites.
Accessing on iPhone (iOS)
- Download the Onion Browser: Onion Browser is the official Tor app for iOS, available in the App Store.
- Install a VPN app for iOS: Open your VPN app and connect to a server outside of your home country.
- Start Onion Browser: With your VPN enabled, launch Onion Browser and enter your .onion URLs as needed.
Accessing on Android
- Download the Tor Browser from Google Play. Make sure it’s the official app published by The Tor Project. You can download the official Tor Browser from Google Play here.
- Install and enable your VPN app on Android.
- Launch the Tor Browser and connect to the Tor network.
Tor Over VPN vs. VPN Over Tor: Which Should You Use?
So far, we have shown you how to connect to Tor over VPN. But you can also connect VPN over Tor. Learn a little more about each approach to help you decide how you want to connect.
Tor Over VPN
Browser to access the Tor network. In this setup, the VPN connection acts as a middle layer between your device and Tor, routing your internet traffic through the VPN before it reaches the Tor network.
How It Works: Tor over VPN
- You connect to your VPN, masking your IP address from your ISP.
- After the VPN connection is established, you open the Tor Browser.
- Your traffic is first routed through the VPN server and then through Tor’s encrypted network.
Advantages of Tor Over VPN
- Extra Anonymity: Your ISP can’t see that you’re using Tor, as your traffic is encrypted by the VPN. All your ISP sees is an encrypted connection to the VPN.
- Access to Blocked Tor Networks: Some countries or networks block access to Tor. By connecting to a VPN first, you can bypass these restrictions since the VPN hides your Tor usage.
- VPN Encryption: Your traffic is encrypted by the VPN before it reaches the Tor network, adding an extra layer of security.
Drawbacks of Tor Over VPN
- Potentially Slower Speeds: Since your traffic is routed through both the VPN and Tor, it may reduce your internet speed significantly.
- Trust in the VPN Provider: In this setup, the VPN provider can see your real IP address, meaning you’re relying on their privacy policies to keep your data secure.
Best For: Users who want to obscure their Tor usage from their ISP or live in regions where Tor access is restricted. Tor over VPN is also ideal for people who already trust their VPN provider and want to increase their anonymity with the added protection of the Tor network.
VPN Over Tor
VPN over Tor is the reverse setup: you connect to the Tor network first, then connect to a VPN. In this method, your traffic is routed through Tor before it reaches the VPN server, masking your IP address even from the VPN provider.
How It Works: VPN over Tor
- You open the Tor Browser, which automatically connects you to the Tor network.
- After connecting to Tor, you then enable the VPN, which routes your traffic through the VPN server after it has passed through the Tor network.
Advantages of VPN Over Tor
- Complete Anonymity from the VPN Provider: Since you’re connecting to Tor first, the VPN provider cannot see your real IP address. This setup protects your identity from both your ISP and the VPN provider.
- Access to Georestricted Content: VPN over Tor can allow you to access sites or content restricted by location, as you can choose a VPN server in a specific region. This benefit is especially useful on the dark web if you need access to regionally restricted services.
Drawbacks of VPN Over Tor
- Complex Setup: VPN over Tor is more challenging to configure, as most VPN providers don’t directly support this setup. You may need to configure Tor settings manually or set up a custom VPN/Tor connection.
- Reduced Speed: As with Tor over VPN, routing your traffic through both Tor and a VPN can significantly slow down your connection.
- Less Popular: VPN over Tor is less commonly supported by VPN providers and can be less reliable. Fewer resources are available for troubleshooting this setup.
Best For: Highly privacy-conscious users who want to hide their IP address from the VPN provider, or those who specifically need location-based access on the dark web.
How to Access Tor via Tails OS on a USB Thumb Drive
Accessing the Tor network through Tails OS (The Amnesic Incognito Live System) on a thumb drive is a highly secure way to browse the dark web anonymously. Tails is a portable operating system specifically designed for privacy, and it includes the Tor Browser by default. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor.
Guide to Accessing Tor via Tails OS on a USB Thumb Drive:
Step 1: Prepare Your Materials
- USB Thumb Drive: Get a USB drive with at least 8GB of storage.
- Download Tails OS: Visit the Tails website to download the latest Tails OS image.
- Tails Installer Software: For this guide, we’ll use Etcher (available on etcher.io) to create a bootable Tails USB drive, which is compatible with Windows, macOS, and Linux.
Step 2: Download and Verify the Tails OS Image
- Download the Tails OS Image: On the Tails website, click “Get Tails” and download the latest version of Tails OS.
- Verify the Download: For extra security, Tails provides a verification tool on their website to confirm your downloaded image file hasn’t been tampered with.

Step 3: Install Tails on the USB Drive
- Open Etcher: Launch the Etcher software you downloaded.
- Select the Tails Image File: In Etcher, click “Flash from file” and choose the Tails image file you downloaded.
- Select the USB Drive: Insert your USB drive, then select it in Etcher as the target drive.
- Flash the Drive: Click “Flash!” to write the Tails OS image to the USB drive. This process may take a few minutes.
Step 4: Boot into Tails OS from the USB Drive
- Restart Your Computer: Leave the USB drive inserted, then reboot your computer.
- Enter BIOS/Boot Menu: While your computer restarts, access the BIOS or boot menu by pressing a specific key (often F12, F2, Esc, or Del, depending on your device). This step allows you to select your USB drive as the boot device.
- Select the USB Drive: Choose the USB drive with Tails OS as the boot option. Your computer should now boot directly into Tails OS.
Step 5: Configure and Start Tails OS
- Choose Your Language and Region: When Tails loads, select your language and region on the welcome screen.
- Configure Additional Settings (Optional): If you need to configure additional settings, such as setting up persistent storage (only available on a secondary USB drive), do so here.
- Start Tails: Click “Start Tails” to load the Tails desktop.
Step 6: Access the Tor Browser on Tails OS
- Open the Tor Browser: Once Tails has loaded, locate the Tor Browser icon on the Tails desktop and click it to open.
- Connect to the Tor Network: The Tor Browser will prompt you to connect to the Tor network. Click “Connect” and wait a few moments for Tor to establish a secure connection.
Step 7: Browse the Dark Web with Tor
Once connected to Tor, you’re ready to browse the dark web. You can enter .onion URLs directly into the Tor Browser’s address bar or visit directories like The Hidden Wiki to find popular sites on the dark web.
Tor-Enabled OS Alternatives to Tails for Secure Dark Web Browsing
Here are some additional alternatives to Tails OS for accessing the dark web securely:
- Whonix: Uses Tor within a virtual machine, isolating internet traffic for strong security. Requires VirtualBox or KVM.
- Qubes OS: A highly secure OS that compartmentalizes activities into isolated “qubes.” Can run Whonix within a qube for dark web access.
- Kodachi Linux: Debian-based, routes traffic through both a VPN and Tor by default. Portable, runs from a USB.
- Liberté Linux: Lightweight, USB-bootable OS focused on secure communication through Tor, with encrypted tools for privacy.
- Parrot Security OS (Home Edition): Privacy-focused OS with Tor pre-installed, available for installation or USB. Versatile and customizable.
Each of these options offers unique privacy features, with Whonix and Qubes for higher security setups, and Kodachi and Liberté for portability.
Browsing Dark Web Domains on Tor
Dark web sites via Tor have unique URL structures that end in .onion. Here’s what you need to know:
.onion URL Structure
These addresses are designed to keep both the site and user anonymous. A typical .onion URL looks like this:
Example .onion URL: http://g7ejphhubv5idbbu3hb3wawrs5adw7tkx7yjabnf65xtzztgg4hcsqqd.onion/
Since .onion URLs can be complex and random, consider bookmarking reliable sites in Tor for easier access.
Accessing the Dark Web Without Tor: Setting Up I2P and Hyphanet
While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing. Let’s go through the setup process for each, as well as how to use them effectively.
Setting Up I2P (Invisible Internet Project)
I2P (Invisible Internet Project) is an open-source network designed to allow anonymous and private communication. Although it’s not as widely used as Tor, I2P can provide robust anonymity and is well-suited for peer-to-peer file sharing.
Step 1: Download I2P
- Visit the I2P website: Go to the official I2P website at https://geti2p.net.
- Download the installer: Click on the download link, then save the installer file to your device.
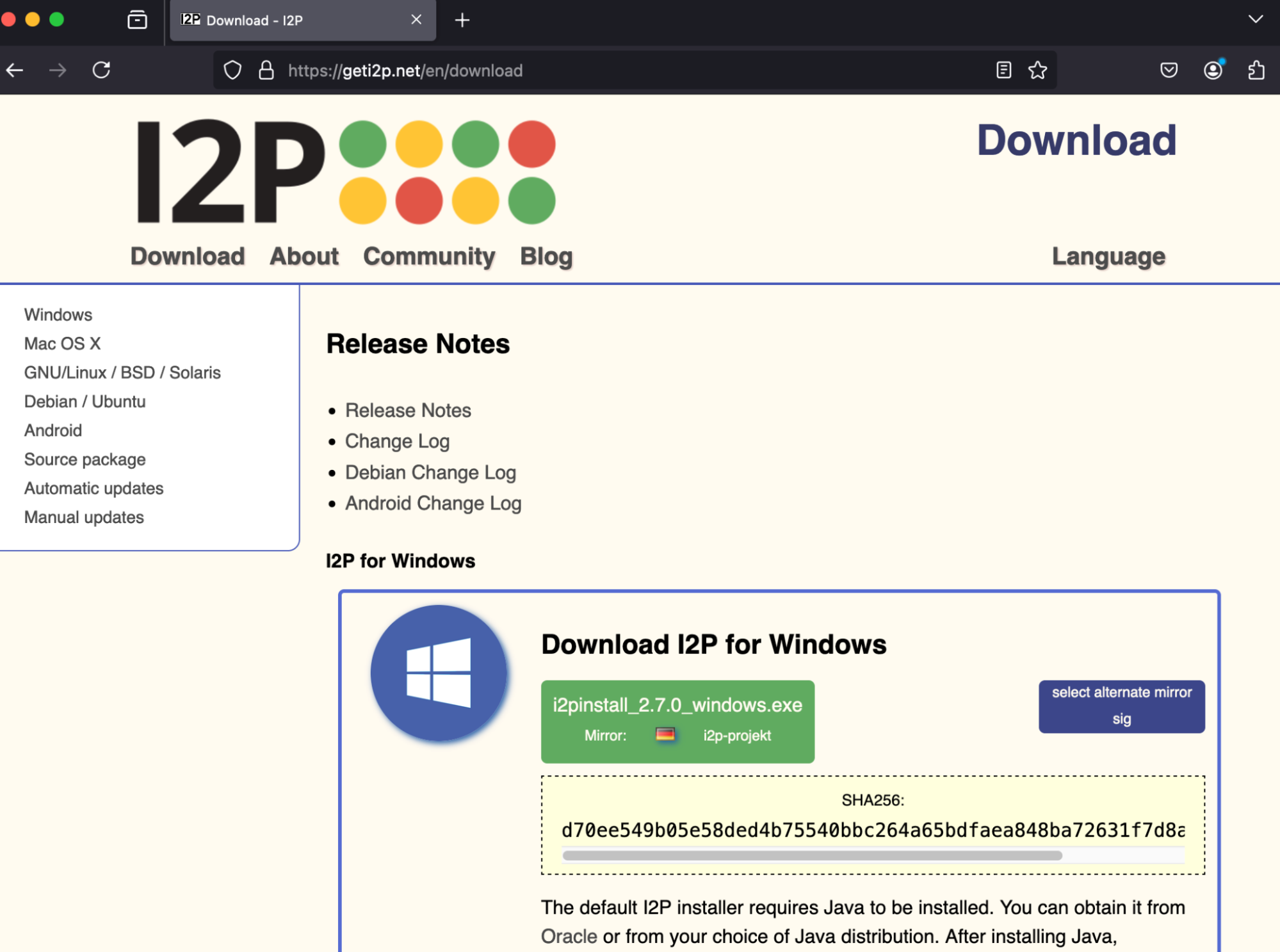
Select your operating system: Choose the installer that matches your OS (Windows, macOS, or Linux).
Step 2: Install I2P
- Run the installer: Once downloaded, open the installer file. Follow the on-screen instructions to complete the installation process.
- Set your installation preferences: You may be prompted to select a location for installation or adjust security settings. Follow the recommended options for a standard setup.
Step 3: Start I2P
- Open the I2P Router Console: After installation, open the I2P Router Console (this is I2P’s control panel) from your Start Menu (Windows) or Applications folder (macOS).
- Wait for I2P to initialize: The I2P Router Console will take a few minutes to initialize and connect to peers on the network. The console interface will show the status as “Active” once it’s fully connected.
Step 4: Access I2P Sites (Eepsites)
- Use the built-in browser (optional): I2P includes a built-in web browser that you can use to access sites on the network, known as “eepsites.”
- Browse eepsites: In the I2P Router Console, navigate to the “Eepsites” section, where you’ll find some popular I2P sites. You can also enter the .i2p addresses of specific sites you want to visit directly into the address bar.
Step 5: Advanced Configuration (Optional)
For advanced users, I2P offers configuration options for adjusting bandwidth limits, adding encryption layers, or even setting up your own eepsites. These settings can be found in the Router Console’s configuration panel.
Setting Up Hyphanet (formerly Freenet)
Hyphanet (formerly Freenet) is another anonymous network that allows you to share and retrieve information without censorship. It’s designed for secure, decentralized storage and is often used for file sharing and accessing information anonymously.
Step 1: Download Hyphanet
- Visit the Hyphanet website: Go to https://www.hyphanet.org/index.html and click the download link.
- Select your OS: Hyphanet provides options for Windows, macOS, and Linux. Download the appropriate installer for your operating system.
Step 2: Install Hyphanet
- Run the installer: After the file downloads, open it to begin the installation process.
- Follow the prompts: Hyphanet’s installation wizard will guide you through the setup. Choose the recommended installation settings for simplicity, or customize if you prefer more control.
Step 3: Launch Hyphanet
- Open Hyphanet: Once installed, launch Hyphanet from your Start Menu (Windows) or Applications folder (macOS).
- Initialize Hyphanet: The first time you run Hyphanet, it may take several minutes to initialize. Hyphanet will automatically connect to the network and synchronize with peers, preparing you for anonymous browsing.
Step 4: Configure Basic Settings
- Choose a security level: Hyphanet offers security level options depending on how private you want your browsing to be. Choose “High” if you’re aiming for the highest privacy level, which restricts who can access your files and messages.
- Adjust bandwidth settings: You can set Hyphanet to use a specific amount of bandwidth, which is useful if you want to limit its impact on your network speed.
Step 5: Start Browsing Hyphanet
- Access Freenet sites (Freesites): Within Hyphanet you can browse decentralized websites known as “freesites.” Use the built-in search or directory to find popular sites and resources.
- Use Hyphanet for file sharing: Hyphanet is often used for peer-to-peer file sharing. You can upload files for secure storage or retrieve files anonymously, knowing that your activity is hidden from prying eyes.
Step 6: Advanced Hyphanet Features (Optional)
For more advanced use, Hyphanet allows you to create and host your own freesites, participate in forums, and communicate anonymously with other users. These features are accessible from the Freenet interface under the “Community” and “Tools” sections.
For detailed instructions and additional resources, refer to the Hyphanet documentation.
By following these steps, you’ll have I2P and Hyphanet set up for secure and private browsing on the dark web. Both networks have unique strengths, and while they aren’t as user-friendly as Tor, they offer excellent alternatives for those seeking robust privacy and decentralized communication options.
Safety Precautions for Accessing the Dark Web
Browsing the dark web requires diligence. Here are best practices to stay safe:
1. Maintain Anonymity
Do not use any personally identifiable information on the dark web. This includes email addresses, usernames, and payment details. Use aliases and avoid any activity that might reveal your identity.
2. Use Secure Connections
Only access the dark web with both a VPN and the Tor Browser active. Avoid altering any security settings in Tor that could reduce your protection.
3. Be Cautious with Downloads
Exercise extreme caution with downloads. Files on the dark web may contain malware, and it's best to avoid downloading from unknown sources.
4. Understand Legal Implications
Certain activities on the dark web are illegal in many countries. Ensure that you’re aware of what is permissible in your jurisdiction.
5. Use a Dedicated Device or Virtual Machine
For added security, use a separate device or virtual machine (VM) when accessing the dark web. A VM can act as a protective barrier between your main device and any potential threats.
6. Regularly Update Your Software
Keeping your VPN and Tor Browser updated ensures you benefit from the latest security patches. Outdated software can have vulnerabilities that may put you at risk.
7. Avoid Sharing Personal Information
Never share real information on the dark web, even in encrypted communications. This rule applies to social media accounts, emails, and purchases.
Wrap-Up: Staying Safe While Accessing the Dark Web
Accessing the dark web is safe and straightforward when you use the right tools and follow best practices. Whether you’re a privacy advocate, journalist, or curious user, using this guide as your foundation will allow you to navigate the dark web responsibly. Just remember: the dark web prioritizes privacy and security, so always take the necessary steps to protect yourself.










